Digital transformation has touched every part of business as people grow increasingly dependent on computers, mobile phones, and other gadgets. On a daily basis, businesses acquire, store, and analyze massive volumes of data, underlining the necessity of data management.
The digital age has resulted in a vast amount of data being created and circulated over the internet. Each person created around 1.7MB of data in 2020, in fact Over 90% of the world’s total data has been generated in the last two years.
These incredible statistics also highlight the critical necessity of security in today’s digital environment. With the advancement of technology, data breaches have grown more frequent. As a result, hackers find it simpler to exploit company vulnerabilities and gain access to private client information.
Digital transformation has fueled the growth of online platforms, emphasizing the need for security in the digital era. If businesses of all kinds, large and small, want to avoid becoming victims of cybercrime, they must handle cyber security.
Security in the modern age
Changes brought on by the epidemic, like remote working, more firms going online, and the use of digital payment, have resulted in an increase in digital risks. But data breaches and cyber threats have been around from before the pandemic. 2016 witnessed the Yahoo security hack, which was an unmitigated disaster.
Other Examples!
Microsoft was hacked in the first quarter of 2020, revealing roughly 250 million customer details, including email addresses, IP addresses, and support case data. In April 2020, a cyber-attack on two websites maintained by San Francisco International Airport was launched, with hackers attempting to gain login information.
Security in theThe importance of Data Security modern age
According to the World Economic Forum’s Global Risks Report, 2021, cyber risk is one of the top global challenges that needs to be addressed immediately.
The digital transformation which is ongoing is ensuring that borders lose meaning each day. In fact, it is data that is transforming us into a global village called Earth. While this is beneficial for organizations trying to expand globally, it also increases the risk of cyber-attacks globally.
Furthermore, every security breach is not only damaging to a company’s image, but it also has a financial impact. Customers will put their faith in a company that has a well-protected cyber security system. This protects the security of any sensitive data, as well as the organization’s long-term viability and efficient operation.
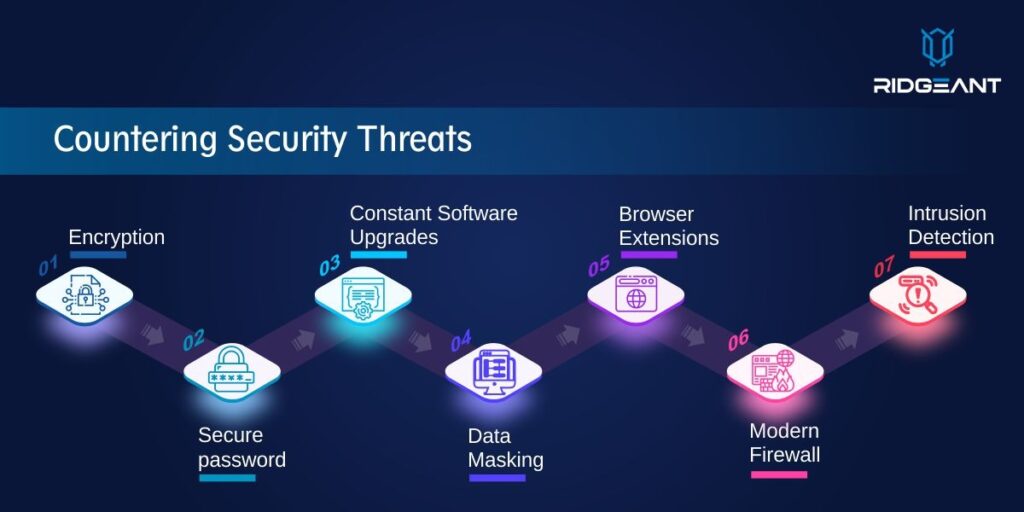
Countering security threats
Organizations must prioritize information security as ransomware, phishing, and social media hacking assaults continue to escalate. This is needed by law since the General Data Protection Regulation (GDPR) requires enterprises in Europe to protect personal information.
To counteract cyber threats, many security procedures are implemented. Here are three practical approaches for businesses to strengthen their cyber defence:
Encryption
Encryption is the most basic yet crucial form of cybersecurity. To prevent email, documents, and other types of data from being abused, stolen, or intercepted by a malevolent third party, it is vital to encrypt them.
Secure password
A strong password that functions as front-line protection is another conventional but equally vital part of cybersecurity. Employees in the office should also be vigilant in the event of phishing attempts, in which hackers send bogus emails in order to steal information. Cyberattacks can be mitigated by increasing awareness and using a safe password.
Constant Software Upgrades
Organizations employ and use a range of software in their everyday operations, and the usage of collaboration tools has expanded as a result of remote setup. Hackers and other digital criminals frequently use such software to obtain access to sensitive data, therefore it’s critical to keep them up to date. Many modifications are made as a result of this, including software updates that address susceptible areas that hackers can access and exploit.
Data Masking
Data masking is a method of protecting original data by creating an exact replica for training or testing. Sensitive data can be safeguarded by changing original data that would be of minimal use to third-party intrusions.
Safe & Secure Browser Extensions
The browser is an indispensable part of everyday digital lives, saving sensitive information such as passwords, financial information, communications, and e-commerce transactions.
Security browser extensions are becoming increasingly vital for safeguarding browsing activities and swiftly analyzing an online service or website for potential risks. They block hazardous sites, give real-time updates, prevent data leakage, and secure your critical information.
Install Modern Firewall and Intrusion Detection Systems
Despite the fact that they both deal with network security, an intrusion detection system (IDS) varies from a firewall in that the latter searches for intrusions from the outside in order to prevent them. Firewalls prevent infiltration by limiting access between networks and do not notify an attack from within the network.
Education
One of the most common reasons for data breaches is human error. Most data breaches may be avoided by teaching your employees how to recognize dangers and respond to illegal activity.
Organizations can use a variety of training initiatives to optimize human potential in the face of cybercrime and prevent employees from circumventing critical security protections.
Conclusion
Digital technology has grown increasingly important in today’s environment. Because of this reliance, cyber-threats have become a part of everyone’s daily lives. Therefore, cybersecurity is more vital than it has ever been. Understanding what you are exposed to online and how to defend yourself from prospective threats is important.
We must anticipate that cyber-attacks and breaches will occur in the future; it is nearly impossible to forecast when and where an attack will occur. The way we respond to and neutralize these threats determines our success.
This will prove to be the greatest protection, as threats may be dealt with before they have a chance to cause major harm by providing organizations with the proper tools and know-how to cope with cyber assaults.
Cyber attacks are here to stay for the foreseeable future, and now is the time to rethink your security approach if you haven’t already. With cyber security taking center stage in an increasingly digital environment, it is more important than ever for everyone to collaborate to keep oneself secure.